Table of contents
This is a writeup for a challenge from PortSwigger's Web Security Academy. In this one, we will learn how a Remote Code Execution vulnerability can be identified and exploited and what an attacker can gain from it.
Objective
This lab contains a vulnerable image upload function. It doesn't perform any validation on the files users upload before storing them on the server's filesystem.
To solve the lab, upload a basic PHP web shell and use it to exfiltrate the contents of the file
/home/carlos/secret. Submit this secret using the button provided in the lab banner.You can log in to your own account using the following credentials:
wiener:peter
> Solving the challenge
We got the website, let's log in with wiener:peter as credentials:

Here we can find a file upload feature:
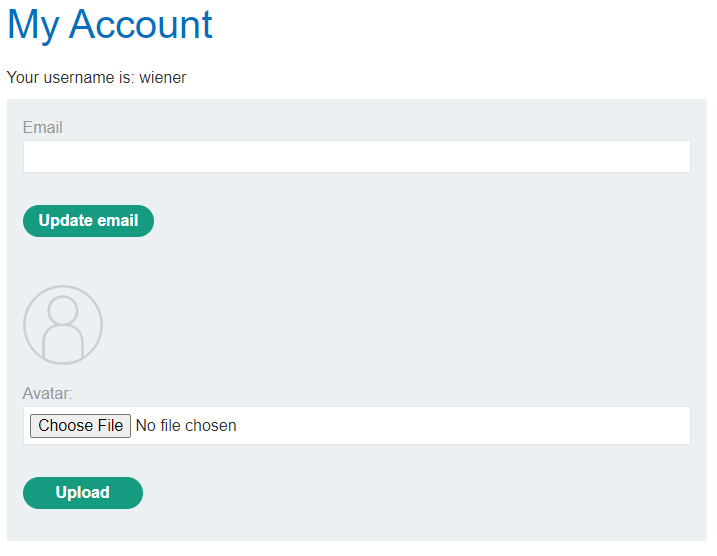
The server seems to expect any type of file, and not just images. As the objective says, let's try to upload some PHP code. I would like to spawn a web shell there, and my PHP web shell of choice is p0wny.
We can upload it via the avatar upload form:
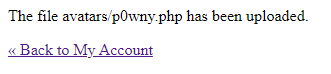
Now we can navigate to the /files/avatars/p0wny.php to spawn a shell:

Apparently, they don't want you to run any type of shell, so I couldn't make it work properly (which is weird, as the title clearly says "Remote code execution via web shell upload"). Same with a more classic reverse shell.
What a shame. Anyway, our goal is to read the flag.
We can create a lame PHP document with something like, as we know what exactly we should read:
<?php echo file_get_contents('/home/carlos/secret'); ?>
Upload your lame.php, and call it as we did with a shell.
Submit the secret to solve the lab: